|
Real cyber-security is more than just protection against cyber-attacks by putting up firewalls and controlling access. It is fully controlling the actions within activities which can have devasting impacts by requiring approval for them to continue, regardless if they were accessed & started somehow. In today's AI world, the embedment of HI into systems is becoming especially important. |
|
|
Get Approvals Now |
|
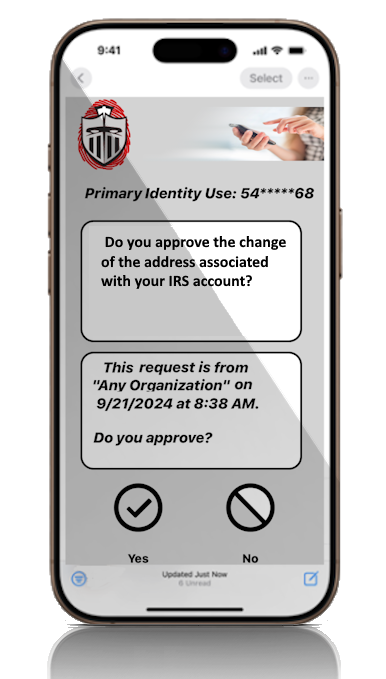
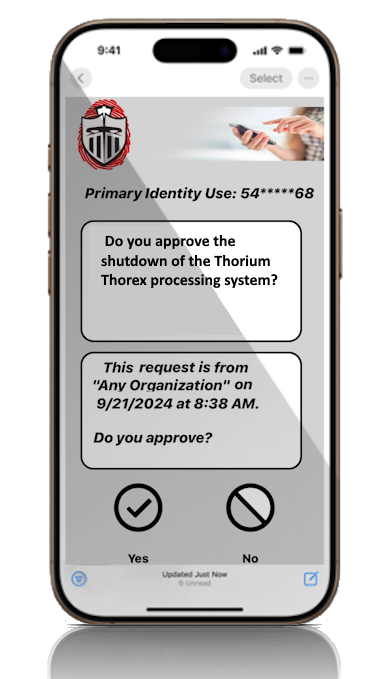
You can contact any individual with Sentry, the personal cyber-security guard, in their lives to obtain approval for any action to continue to which they are associated. There is no limit to the types of actions, in any industry, to be controlled before proceeding. Activities such as common business steps, i.e., use of a taxpayer's SSN to modify the address used for tax refunds, a manager's user id to authorize anything like turning off an electrical grid, or somebody's credit card to make a purchase online for a 85" tv.
You can manually get approval here for any actions in any activity to continue or stop it from becoming a problem if you have their related Sentry activated identity and use it. Select the type of identity use below to proceed. Your organization can also easily add this capability directly into its systems.
|
|
Overview |
|
Real cyber-security consists of Authentication, Authorization, Approval & Accounting.
Authentication is “Verify an Identity” while Authorization is “Give Permissions”, Approval is “Make a Decision” and Accounting is "Record Events". Today, together, Authentication and Authorization control access of an identity to an application with its activities consisting of actions with Accounting recording the cyber-security event details.
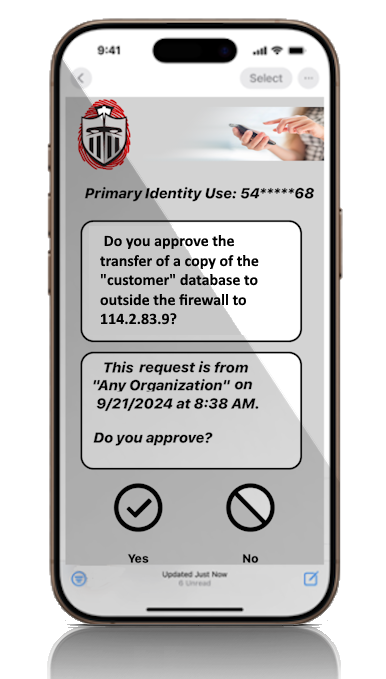
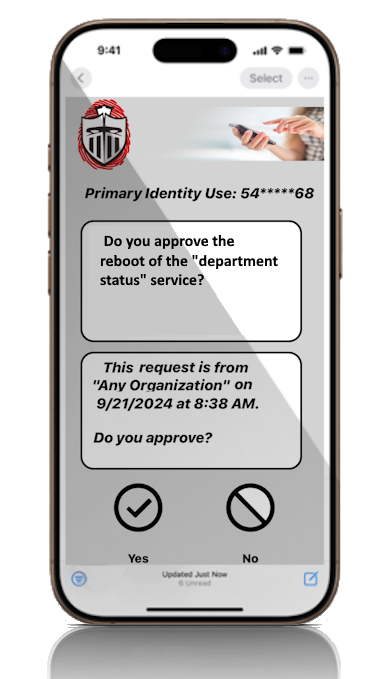
What is missing is "Approval" which requires a second “positive” decision from an approver to be made before an activity or an action proceeds to run. There is a big difference between controlling access to an action vs the action controlling itself. Sentry is an "action approval" service that empowers an application to obtain real-time approval before any initiated actions with possible negative impacts can continue execution. Real-time approval from a specified individual or group.
Unlike authentication and IAM applications which are external to the application's actions, Sentry services are added as very small modifications of the application actions themselves preventing possible manipulation. Authentication and IAM applications, even if multi-factored, only control access to an application. Sentry enables an application to confirm an action’s continuation from one or more real people, i.e. “Multi-Factor Approval”. Applications can be updated with “action approval” of multiple, different actions targeting various individuals or groups for absolute control. The required approval response time periods are definable for each action and each action approval request.
With the number of cyber-attacks, both criminal & terrorist, continuing to grow and targeting individuals, businesses and governments from every demographic, having a service that can give complete & secure control of any organization’s processes is absolutely vital. Identity Checkpoint’s cloud-based, patented Sentry services & “action approval” application together provide comfort and peace of mind in a time where a moment of inattention and/or no control can be devastating.
Have AAA+ Cyber-Security at all times.
|
|
Understand Getting Approvals |
|
Master getting action approvals for the most scenarios. Start by watching the short video below on the left. Then start discovering how to use this site to get action approvals for the different identity uses show below. Finally, discover and get the Sentry application for devices by selecting the devices image.
|
|
Features |
|
|
|
|
|
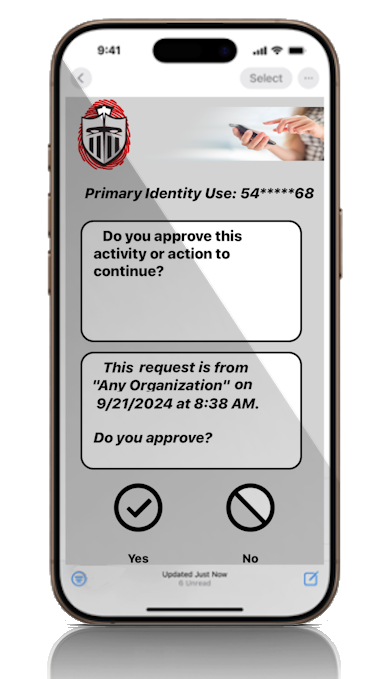
Manage the continuance of the initialization of any system action by obtaining approval from the designated individuals' registered devices using Sentry services. If not obtained, the default approval is "No". |
Sentry's interactive approval cloud service connects with the approver(s) using the Internet to basically ask a question and get approval before specific actions with possible negative impacts truly start. |
With today’s cyber-attacks being responsible for trillions of dollars in cyber-security costs & lost assets annually, Identity Checkpoint's Sentry services will help keep most of our money right where it belongs. |
|
|
Benefits |
|
|
Losing control of IT processes can have immense and long-lasting consequences. The search for effective solutions to manage identity authentication and system access continues to be a challenge, especially in the face of successful cyber-attacks on major organizations. The stress and complexity of dealing with such loss of control are burdens that no individual or entity should bear. Opting for Identity Checkpoint and Sentry provides real-time, lifelong protection that is more than traditional AAA cyber-security has provided. Making this choice ensures control of your systems and can provide a safe and secure environment for your valuable data and digital assets that you can trust. For more details, click the brochure below. |
|
|
Examples |
|
|
|
|
|
|
|